Security in the Age of AI oracle.com CHECK POINT 2013 SECURITY REPORT 01 _ INTRODUCTION AND METHODOLOGY sensitive data loss, etc. The network traffic was monitored in real time by implementing the Check Point Security Gateway inline or in monitor (i.e. tap) mode. On average, each organization’s network traffic was
Annual Security Report for 2018
2019 Annual Security and Fire Safety Report. The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security., 4 REPORT ON CYBERSECURITY PRACTICES—FEBRUARY 2015 Given this definition, not all issues we discuss in this report are viewed by firms as within the scope of their cybersecurity program. For example, some firms would address fraudulent wire transfers carried out through socially engineered phishing attacks through their anti-fraud, rather than.
Risk Based Security, 2018) 1, PDF, accessed on February 21, 2018 Web applications represented 51% of disclosed vulnerability issues in 2017. Report 201 Application Security Research Update 6 Figure 5. Operating systems with the highest volume of vulnerabilities reported in 2017 (NVD) . However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and
security at Cal Poly Pomona and to comply with the Jeanne Clery Disclosure of Campus Security Policies and Campus Crime Statistics Act (hereafter the Clery Act or Clery). This report complies with state and federal crime awareness and campus security legislation, including the Clery Act, California Education Code section 67380, the security at Cal Poly Pomona and to comply with the Jeanne Clery Disclosure of Campus Security Policies and Campus Crime Statistics Act (hereafter the Clery Act or Clery). This report complies with state and federal crime awareness and campus security legislation, including the Clery Act, California Education Code section 67380, the
SECURITY IN THE AGE OF AI A report on the views and actions of C-Suite executives, policy makers and the public related to cybersecurity and data protection in today’s threat-filled world The Annual Security and Fire Report demonstrates our commitment. Key Sections of this report can be found: Table of Contents begins on page 4 2016-2018 Crime Statistics begin on page 101 2016-2018 Fire Statistics begin on page 128 ^It is in your interest! This is because our effectiveness in maintaining a safe campus environment depends on you.
from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com. Security may choose to deploy authorized armed security personnel as needed. A security presence is provided by the property managers at the West Florida Learning Center and Dallas Campus. However, these buildings В¶ security guards do not have the authority to make arrests and are not affiliated with University of Phoenix Corporate Security.
However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and 7-11-2019В В· Today every business is a mobile business, with requirements to safeguard business data, provide secure mobile access to business documents and keep mobile devices safe from threats. Check Point enterprise mobile security solutions provide the widest range of products to help you secure your mobile world.
This report also includes institutional policies concerning campus security, such as policies concerning alcohol and drug use, crime prevention, the … Physical security products and services initiatives 42 Control products and systems initiatives 44 Initiatives to enhance organizations 46 Research and development 48 〈Overview of this report〉 Scope of this report: This report covers information security initiatives taken by the Hitachi Group in FY 2017 and earlier.
Telstra Security Report 2019 – Summary Report 6. The Broadening Security Landscape This year, 100 per cent of respondents identified that within their role they were responsible for both cyber and electronic security within their organisation. Physical security products and services initiatives 42 Control products and systems initiatives 44 Initiatives to enhance organizations 46 Research and development 48 〈Overview of this report〉 Scope of this report: This report covers information security initiatives taken by the Hitachi Group in FY 2017 and earlier.
tive security into intelligent security. This will be enabled by report-ing, analyzing and using large volumes of data, and leveraging the largely unutilized database we have at our customers’ sites. Using both historical and real-time data that is generated by our security officers, as well as equipment such as sensors and Over the past decade, Cisco has published a wealth of security and threat intelligence information for security professionals interested in the state of global cybersecurity. These comprehensive reports have provided detailed accounts of threat landscapes and their effects on organizations, as well as best practices to defend against the adverse impacts of data breaches.
guidance provided in this report useful in helping them protect their organizations, software, and users. Reporting period This volume of the Microsoft Security Intelligence Report focuses on the first and second quarters of 2012, with trend data for the last several years presented on a … from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com.
and France, the iPass Mobile Security Report 2017 overviews how organizations are dealing with the trade-off between enforcing security policies and enabling a mobile workforce. The report’s findings include the following: • Organizations consider C-level employees, including the CEO, to be at the greatest risk of being hacked. Microsoft announces new innovations in security, compliance, and identity at Ignite Top 10 announcements from the Microsoft Ignite Conference across security, compliance, and identity. Read more Microsoft announces new innovations in security, compliance, and identity at Ignite
The Telstra Security Report 2018 provides insights into the current security landscape, to help arm organisations with research based information on managing and mitigating their risk. This year, we have extended the scope of our research to include electronic security. For the purpose of this report, electronic security refers security in their organizations, Cisco asked chief information security oŠcers (CISOs) and security operations (SecOps) managers in nine countries and at organizations of diŒerent sizes about their security resources and procedures. The study’s ndings are exclusive to the Cisco 2015 Annual Security Report. 3. Geopolitical and Industry Trends
APPLICATION SECURITY IN THE CHANGING RISK LANDSCAPE
FACTS AND FIGURES SECURITY REPORT 2016/17 AV-TEST. However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and, SECURITY IN THE AGE OF AI A report on the views and actions of C-Suite executives, policy makers and the public related to cybersecurity and data protection in today’s threat-filled world.
2019 UOPX Annual Security Report University of Phoenix. from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com., 2018 security report 1 contents 44 conclusion 40 platform 34 2018: the road ahead recommendations 21 report by industry latest trends across the 15 cyber security landscape.
ANNUAL Security Fire Safety d3qi0qp55mx5f5.cloudfront.net
Android Security & Privacy 2018 Year In Review. evaluation of our efforts. To that end, we present the Annual Security and Fire Safety Report. This report is provided in compliance with the Jeanne Clery Disclosure of Campus Security Policy and Campus Crime Statistics Act (Clery Act}, the Higher Education Opportunity Act (HEOA}, and the Violence Against Women Reauthorization Act of 2013 (VAWA). https://upload.wikimedia.org/wikipedia/commons/4/4a/Nsa-ig-draft-report.pdf tive security into intelligent security. This will be enabled by report-ing, analyzing and using large volumes of data, and leveraging the largely unutilized database we have at our customers’ sites. Using both historical and real-time data that is generated by our security officers, as well as equipment such as sensors and.
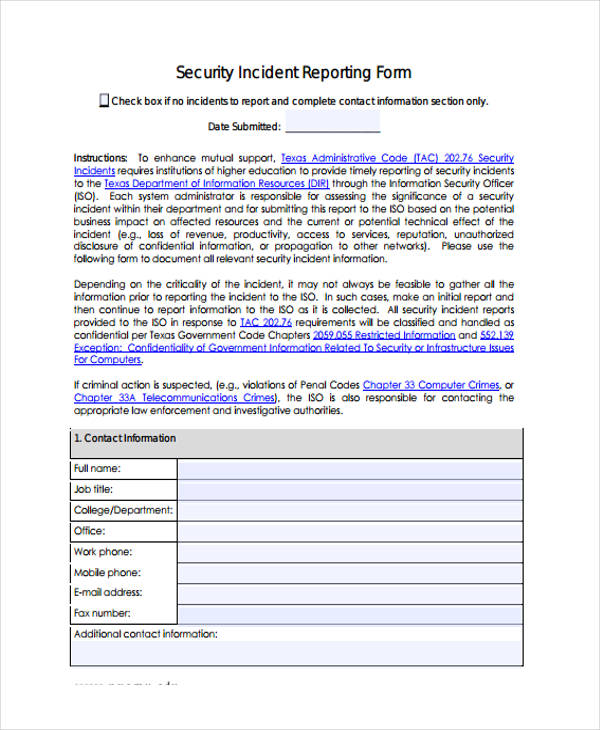
The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security. We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices.
However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and Legacy security tools limited in the cloud – Only 16 percent of organizations report that the capabilities of traditional security tools are sufficient to manage security across the cloud, a 6 percentage point drop from our previous survey. Eighty-
We analyze the impacts of new trends including examinations of the shifting environment of network security, how security reach is expanding, new threats, and new areas of vulnerability. Skip to main content Ixia. Go to www.keysight.com . Menu Security Report 2017. from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com.
2018 Mobile Security Report 7 Mobile security challenges remain a huge concern Based on the earlier statistics, it’s not surprising that enter - prises remain concerned about the security risk posed by the growing number of mobile workers. Overall, 92% of organizations said they were very concerned or somewhat The Telstra Security Report 2018 provides insights into the current security landscape, to help arm organisations with research based information on managing and mitigating their risk. This year, we have extended the scope of our research to include electronic security. For the purpose of this report, electronic security refers
Over the past decade, Cisco has published a wealth of security and threat intelligence information for security professionals interested in the state of global cybersecurity. These comprehensive reports have provided detailed accounts of threat landscapes and their effects on organizations, as well as best practices to defend against the adverse impacts of data breaches. We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices.
However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and
Ponemon Institute© Research Report 3 3 Cyber security threats will weaken application security programs, but new IT security and privacy compliance requirements will strengthen these programs. Eighty-eight percent of respondents are concerned that new and emerging cyber security threats will affect the security of applications. 21-12-2018 · We share that insight with you through our products and through intelligence reports such as this. We’ll continue exploring and providing you with new data and insights as the landscape changes and hope that you find value in the Microsoft Security Intelligence Report.
HACKERONE HACKER-POWERED SECURITY REPORT 2017 Introduction Security experts are in high demand as hundreds of millions of lines of new code are deployed each day. Hacker-powered security provides a way to identify high-value vulnerabilities faster, leveraging the creativity of the world’s largest ethical hacker community. 2018 security report 1 contents 44 conclusion 40 platform 34 2018: the road ahead recommendations 21 report by industry latest trends across the 15 cyber security landscape
from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com. Report 2011 highlights the issue of security for national aid workers, drawing upon findings from a major survey of national aid workers conducted for a recent OCHA-commissioned study: To Stay and Deliver: Good Practice for Humanitarians in Complex Security Environments (Egeland,
Physical security products and services initiatives 42 Control products and systems initiatives 44 Initiatives to enhance organizations 46 Research and development 48 〈Overview of this report〉 Scope of this report: This report covers information security initiatives taken by the Hitachi Group in FY 2017 and earlier. security in their organizations, Cisco asked chief information security oŠcers (CISOs) and security operations (SecOps) managers in nine countries and at organizations of diŒerent sizes about their security resources and procedures. The study’s ndings are exclusive to the Cisco 2015 Annual Security Report. 3. Geopolitical and Industry Trends
We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices. The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security.
September 2019 Monthly Forecast Security Council Report
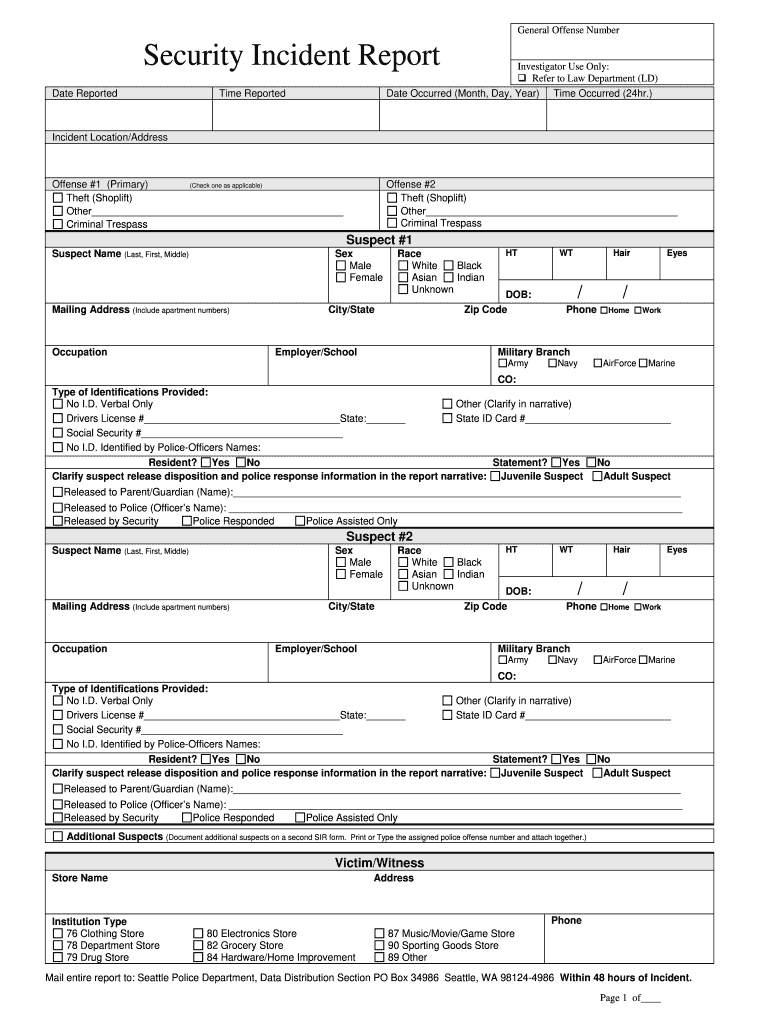
FACTS AND FIGURES SECURITY REPORT 2016/17 AV-TEST. and France, the iPass Mobile Security Report 2017 overviews how organizations are dealing with the trade-off between enforcing security policies and enabling a mobile workforce. The report’s findings include the following: • Organizations consider C-level employees, including the CEO, to be at the greatest risk of being hacked., guidance provided in this report useful in helping them protect their organizations, software, and users. Reporting period This volume of the Microsoft Security Intelligence Report focuses on the first and second quarters of 2012, with trend data for the last several years presented on a ….
ANNUAL SECURITY & FIRE SAFETY REPORT
ANNUAL SECURITY & FIRE SAFETY REPORT. Risk Based Security, 2018) 1, PDF, accessed on February 21, 2018 Web applications represented 51% of disclosed vulnerability issues in 2017. Report 201 Application Security Research Update 6 Figure 5. Operating systems with the highest volume of vulnerabilities reported in 2017 (NVD) ., Telstra Security Report 2019 – Summary Report 6. The Broadening Security Landscape This year, 100 per cent of respondents identified that within their role they were responsible for both cyber and electronic security within their organisation..
HACKERONE HACKER-POWERED SECURITY REPORT 2017 Introduction Security experts are in high demand as hundreds of millions of lines of new code are deployed each day. Hacker-powered security provides a way to identify high-value vulnerabilities faster, leveraging the creativity of the world’s largest ethical hacker community. Security Council Report Executive Director Karin Landgren's briefing to the Council at the open debate on working methods. Insights on the work of the UN Security Council. What's In Blue is a series of insights produced by Security Council Report on evolving Security Council actions.
This Security Report encompasses not only the data status for the year 2016 but also takes into account the measurement results of the AV-TEST analysis systems for the first quarter of 2017. Thus it is already possible to recognize trends for the current year, backed up by data. The Q1-2017 numbers confirm the trend that Apple users will not find We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices.
29-10-2017 · For 20 years, leaders have turned to PwC's Global State of Information Security® Survey (GSISS) as a trusted resource to navigate the cyber risk landscape. Over time, that landscape has evolved to be less about information security and more about managing digital risk. As cybersecurity, privacy and HACKERONE HACKER-POWERED SECURITY REPORT 2017 Introduction Security experts are in high demand as hundreds of millions of lines of new code are deployed each day. Hacker-powered security provides a way to identify high-value vulnerabilities faster, leveraging the creativity of the world’s largest ethical hacker community.
CHECK POINT 2013 SECURITY REPORT 01 _ INTRODUCTION AND METHODOLOGY sensitive data loss, etc. The network traffic was monitored in real time by implementing the Check Point Security Gateway inline or in monitor (i.e. tap) mode. On average, each organization’s network traffic was security at Cal Poly Pomona and to comply with the Jeanne Clery Disclosure of Campus Security Policies and Campus Crime Statistics Act (hereafter the Clery Act or Clery). This report complies with state and federal crime awareness and campus security legislation, including the Clery Act, California Education Code section 67380, the
However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and from across Akamai, including the Security Intelligence Response Team (), the Threat sirt Research Unit, Information Security, and the Custom Analytics group. If you have comments, questions, or suggestions regarding the State of the Internet / Security report, connect with us via email at SOTISecurity@akamai.com.
29-10-2017 · For 20 years, leaders have turned to PwC's Global State of Information Security® Survey (GSISS) as a trusted resource to navigate the cyber risk landscape. Over time, that landscape has evolved to be less about information security and more about managing digital risk. As cybersecurity, privacy and Annual Security & Fire Safety Report 2018–19 1 Welcome to the University of Chicago and Its Community Welcome to Chicago—a vibrant and exciting city of 2.7 million people who live in 77
Risk Based Security, 2018) 1, PDF, accessed on February 21, 2018 Web applications represented 51% of disclosed vulnerability issues in 2017. Report 201 Application Security Research Update 6 Figure 5. Operating systems with the highest volume of vulnerabilities reported in 2017 (NVD) . Telstra Security Report 2019 – Summary Report 6. The Broadening Security Landscape This year, 100 per cent of respondents identified that within their role they were responsible for both cyber and electronic security within their organisation.
guidance provided in this report useful in helping them protect their organizations, software, and users. Reporting period This volume of the Microsoft Security Intelligence Report focuses on the first and second quarters of 2012, with trend data for the last several years presented on a … Security may choose to deploy authorized armed security personnel as needed. A security presence is provided by the property managers at the West Florida Learning Center and Dallas Campus. However, these buildings ¶ security guards do not have the authority to make arrests and are not affiliated with University of Phoenix Corporate Security.
Security incident reports are very important summaries of misdemeanor or criminal incidents that security staff must file not just in accordance to company rules but for police authorities who need a written account of the incident for the filing of an official incident report since incident reports are used for filing of cases and insurance and France, the iPass Mobile Security Report 2017 overviews how organizations are dealing with the trade-off between enforcing security policies and enabling a mobile workforce. The report’s findings include the following: • Organizations consider C-level employees, including the CEO, to be at the greatest risk of being hacked.
7-11-2019В В· Today every business is a mobile business, with requirements to safeguard business data, provide secure mobile access to business documents and keep mobile devices safe from threats. Check Point enterprise mobile security solutions provide the widest range of products to help you secure your mobile world. The Telstra Security Report 2018 provides insights into the current security landscape, to help arm organisations with research based information on managing and mitigating their risk. This year, we have extended the scope of our research to include electronic security. For the purpose of this report, electronic security refers
2018 Mobile Security Report ipass.com
Internet Security Threat Report (ISTR) 2019 Symantec. This report also includes institutional policies concerning campus security, such as policies concerning alcohol and drug use, crime prevention, the …, Telstra Security Report 2019 – Summary Report 6. The Broadening Security Landscape This year, 100 per cent of respondents identified that within their role they were responsible for both cyber and electronic security within their organisation..
2018 CLOUD SECURITY REPORT. Legacy security tools limited in the cloud – Only 16 percent of organizations report that the capabilities of traditional security tools are sufficient to manage security across the cloud, a 6 percentage point drop from our previous survey. Eighty-, 7-11-2019 · Today every business is a mobile business, with requirements to safeguard business data, provide secure mobile access to business documents and keep mobile devices safe from threats. Check Point enterprise mobile security solutions provide the widest range of products to help you secure your mobile world..
2017 Security Report Ixia Ixia Makes Networks Stronger
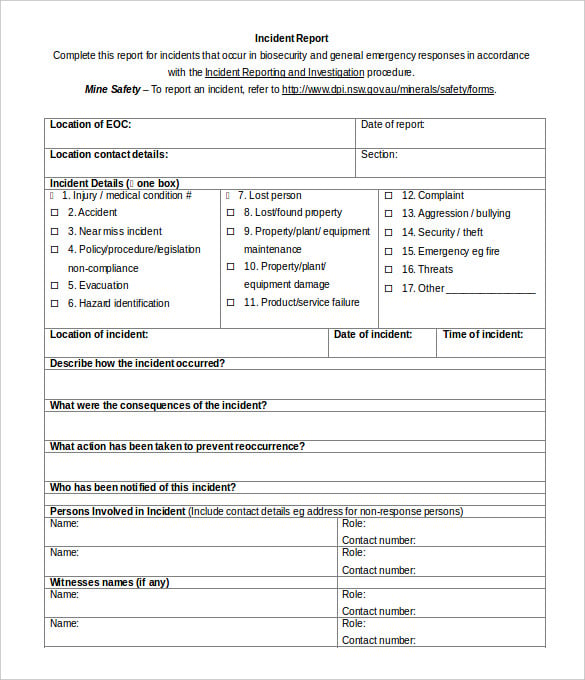
2019 ANNUAL SECURITY REPORT cpp.edu. 4 REPORT ON CYBERSECURITY PRACTICES—FEBRUARY 2015 Given this definition, not all issues we discuss in this report are viewed by firms as within the scope of their cybersecurity program. For example, some firms would address fraudulent wire transfers carried out through socially engineered phishing attacks through their anti-fraud, rather than https://en.wikipedia.org/wiki/Danbury,_Connecticut The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security..

security in their organizations, Cisco asked chief information security oŠcers (CISOs) and security operations (SecOps) managers in nine countries and at organizations of diŒerent sizes about their security resources and procedures. The study’s ndings are exclusive to the Cisco 2015 Annual Security Report. 3. Geopolitical and Industry Trends 7-11-2019 · Today every business is a mobile business, with requirements to safeguard business data, provide secure mobile access to business documents and keep mobile devices safe from threats. Check Point enterprise mobile security solutions provide the widest range of products to help you secure your mobile world.
We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices. This Security Report encompasses not only the data status for the year 2016 but also takes into account the measurement results of the AV-TEST analysis systems for the first quarter of 2017. Thus it is already possible to recognize trends for the current year, backed up by data. The Q1-2017 numbers confirm the trend that Apple users will not find
Annual Security & Fire Safety Report 2018–19 1 Welcome to the University of Chicago and Its Community Welcome to Chicago—a vibrant and exciting city of 2.7 million people who live in 77 Physical security products and services initiatives 42 Control products and systems initiatives 44 Initiatives to enhance organizations 46 Research and development 48 〈Overview of this report〉 Scope of this report: This report covers information security initiatives taken by the Hitachi Group in FY 2017 and earlier.
The Annual Security and Fire Report demonstrates our commitment. Key Sections of this report can be found: Table of Contents begins on page 4 2016-2018 Crime Statistics begin on page 101 2016-2018 Fire Statistics begin on page 128 ^It is in your interest! This is because our effectiveness in maintaining a safe campus environment depends on you. Annual Security & Fire Safety Report 2018–19 1 Welcome to the University of Chicago and Its Community Welcome to Chicago—a vibrant and exciting city of 2.7 million people who live in 77
The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security. Risk Based Security, 2018) 1, PDF, accessed on February 21, 2018 Web applications represented 51% of disclosed vulnerability issues in 2017. Report 201 Application Security Research Update 6 Figure 5. Operating systems with the highest volume of vulnerabilities reported in 2017 (NVD) .
2018 Mobile Security Report 7 Mobile security challenges remain a huge concern Based on the earlier statistics, it’s not surprising that enter - prises remain concerned about the security risk posed by the growing number of mobile workers. Overall, 92% of organizations said they were very concerned or somewhat The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security.
2018 security report 1 contents 44 conclusion 40 platform 34 2018: the road ahead recommendations 21 report by industry latest trends across the 15 cyber security landscape The 2019 Internet Security Threat Report takes a deep dive into the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security.
However, with new technologies come new security concerns. Bad actors have already targeted many blockchain implementations using social engineering, malware, and exploits. As additional groups begin using blockchain and building tools around it, they must understand the security risks. In this report we will look at current security problems and This Security Report encompasses not only the data status for the year 2016 but also takes into account the measurement results of the AV-TEST analysis systems for the first quarter of 2017. Thus it is already possible to recognize trends for the current year, backed up by data. The Q1-2017 numbers confirm the trend that Apple users will not find
Earlier in this report, those surveyed showed a lack of confidence in their current mobile device security and were extremely doubtful of their organization’s ability to prevent an attack. This finding – that only 38% of the companies have a dedicated mobile device security solution – may be the key reason. More than half the organizations tive security into intelligent security. This will be enabled by report-ing, analyzing and using large volumes of data, and leveraging the largely unutilized database we have at our customers’ sites. Using both historical and real-time data that is generated by our security officers, as well as equipment such as sensors and
The Annual Security and Fire Report demonstrates our commitment. Key Sections of this report can be found: Table of Contents begins on page 4 2016-2018 Crime Statistics begin on page 101 2016-2018 Fire Statistics begin on page 128 ^It is in your interest! This is because our effectiveness in maintaining a safe campus environment depends on you. 4 REPORT ON CYBERSECURITY PRACTICES—FEBRUARY 2015 Given this definition, not all issues we discuss in this report are viewed by firms as within the scope of their cybersecurity program. For example, some firms would address fraudulent wire transfers carried out through socially engineered phishing attacks through their anti-fraud, rather than
2018 Mobile Security Report 7 Mobile security challenges remain a huge concern Based on the earlier statistics, it’s not surprising that enter - prises remain concerned about the security risk posed by the growing number of mobile workers. Overall, 92% of organizations said they were very concerned or somewhat evaluation of our efforts. To that end, we present the Annual Security and Fire Safety Report. This report is provided in compliance with the Jeanne Clery Disclosure of Campus Security Policy and Campus Crime Statistics Act (Clery Act}, the Higher Education Opportunity Act (HEOA}, and the Violence Against Women Reauthorization Act of 2013 (VAWA).